Note: I have no affiliation with the City of Rocky Mount and have no insider knowledge outside what has been made publicly available either by press release or interviews with city officials.
On August 14, 2020, my hometown of Rocky Mount, NC experienced a ransomware attack. The City has released certain information about the attack but certain details are left out. This is my attempt to deconstruct possible scenarios based on known attack vector combined with statements from officials.
Conti Ransomware
It is confirmed to be Conti Ransomware. This is believed to the predecessor of Ryuk which is a RaaS (Ransomware as a service). Conti, like many other ransomware attacks, uses Trickbot and Emotet as the initial foothold. Trickbot and Emotet are used to drop other malware or tools onto the infected system in order for the attacker to carry out their attack. This will usually enter a network via email, malvertising, or drive by download. In many instances, the initial compromise will be a brute force attack on an exposed RDP (Remote Desktop Protocol) server. While possible, I do not suspect this to be the case — or I at least hope not as it is had been known for a while that exposing RDP is a very risky setup.
Conti’s Unique (yet powerful) Features
- It is fast: It has been reported that Conti will use up to 32 simultaneous threads to encrypt data.
- Network only encryption mode: Allows Conti to encrypt nearby SMB shares over the network.
- Abuses Windows restart manager to allow access to normally locked files like database files.
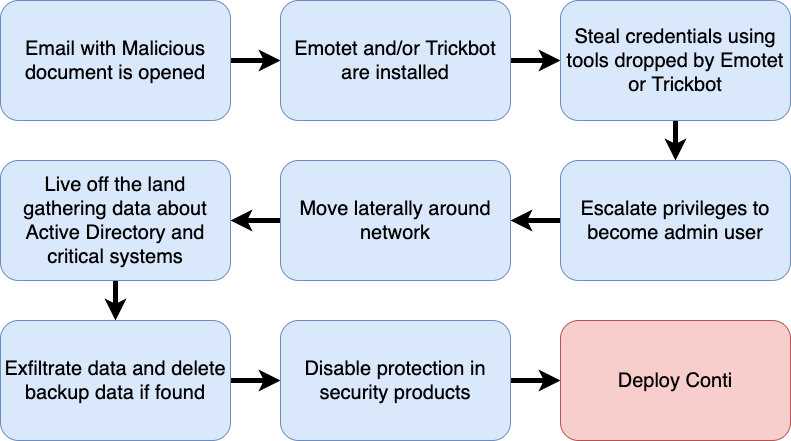
Below is a flow chart showing the normal path a Conti Ransomware attack takes from initial compromise to deployment of Conti itself.
Data Exfiltration
“In addition to causing a computer system disruption, the group responsible for this cyber-attack claim to have stolen City information and are threatening to publicly release the information unless the City pays a ransom” — September 1st Press Release
Conti is also known to exfiltrate data before encrypting to persuade the victim into paying the ransom. Based on the above statement, it would explain why the city is offering free credit monitoring to citizens. The extent of this possible data breach needs to be further investigated to determine scope — which it sounds like they are doing. If they offer free credit monitoring, take it as the information stolen could possibly include name, Social Security number, driver’s license / identification card number, financial account information, credit/debit card, etc.
While we can hope this data was encrypted at rest, it does not mean the attackers were not successful in obtaining this data considering the extent of the attack and admin privileges potentially obtained to carry out the attack.
Act as though this data was indeed breached and follow steps outlined by the City.
Lateral Movement
During the September 2nd press conference, City officials said 15% of endpoints were impacted which points to successful lateral movement within the network. Conti can operate in a fully autonomous mode as well as controlled via an attacker. Based on lateral movement, my assumption is this involved human interaction.
“This particular virus spread quickly, within seconds within three seconds of someone signing in, they can encrypt their computer.”
Based on this comment from city staff from WRAL, We can assume domain admin access was achieved and the ransom payload pushed to computers via a GPO (Group Policy Object).
Targeted Attack?
City officials mentioned they were not targeted. Considering lateral movement and the fact they are a municipality, I don’t buy the idea they were not targeted.
Conti (formally Ryuk) has a track record of targeting municipalities. Direct named target from the attacker? No. Broad target due to being a municipality? Yes.
“Officials also do not know what files were compromised from the attack.”
I have a concern about the lack of details presented about data impacted. This points to the lack of proper logging and auditing of systems. Of course, these measures could have been present and not properly protected themselves resulting in loss of audit data.
Moving forward this is a crucial step the City must take to not only show what data was impacted in a potential future event but also to be able to monitor and audit this protected data in search for indicators of compromise.
Lack of oversight
City officials mentioned they have a vacant CTO role. While this role is crucial, as oversight of a security program is important, the CTO will need additional resources to lean on that focus specifically on security and not just general IT operations. They need to either bring a CISO (Chief Information Security Officer) in house or outsource this to a reliable third party to help determine the current gaps and work towards mitigating those risks. This needs to be an ongoing effort and not just a one-time bandaid to resolve the current issue.
While this post may seem as though I am pointing fingers and blaming the City for this incident, I am not. Cybersecurity is not easy and having a mature security posture is time-consuming and costly.
Mitigation Suggestions
- Remove local admin for all users (Audit this with PingCastle)
- Do not log in as domain admin on workstations (seriously, stop this)
- Setup LAPS to change local admin password (It is free, just do it)
- Segment your network to make lateral movement difficult
- Use at least 15 character passwords for Users and 25 character for Service accounts (if a password hash is stolen, 15 characters becomes difficult to crack)
- Disable LLMNR (Link-Local Multicast Name Resolution) and NBNS (NetBios)
- Disable IPv6 if not used on your network. Stops broadcast of IPv6 traffic that may be intercepted by tools such as MITM6.
- Enable SMB Signing and disable SMBv1
- Deploy a EDR solution such as SentinelOne, Crowdstrike, Sophos Intercept X with EDR, etc.
- Whitelist applications via GPO, AppLocker, or software solutions like Threatlocker.
- Deploy MFA (Multi-factor authentication) at the endpoint and server for privileged access. Make sure offline mode is enforced. Duo offers their MFA edition for free up to 10 users.
- Watch systems for use of cloud services such as MegaUpload which are commonly used to exfiltrate data.
- Block macros in Office documents, preferably by GPO.
- If you have RDP exposed, by all means stop. If not possible to tuck away behind a VPN, implement a RDP gateway. No RDP gateway option use an IPS like RDP Guard.
- Protect DNS queries with services like Quad9 (Free), OpenDNS, DNSFilter, Webroot DNS, etc.
- Monitor for clearing of system event logs as this is a step many attackers take before final deployment.
- Setup Canary Tokens and distribute strategically throughout environment.
- Train employees on how to spot Phishing or Malicious emails. Knowbe4 is a great resource.
These are just a few things that help stop lateral movement attacks but are by no means a bullet proof vest.

